Hello Readers,
Welcome to the 5th blog of "AzureAdB2c series". In the first 4 parts we have seen how to create Azure AD B2C Tenant step by step , how to use it with .net core application and what are the different "Identity Providers In Azure Active Directory B2C" and how to add google account as identity provider. If you haven't checked yet then you can check Part-1 - Part-2-Part-3-Part-4. So, Today we will look into add google account as identity provider in azure active directory b2c tenant.
Why Integrate Azure AD B2C with Google Accounts?
In today's fast-paced digital landscape, organizations strive to provide seamless user experiences while ensuring top-notch security. Azure Active Directory B2C (Azure AD B2C) offers a robust identity management solution that enables businesses to integrate with various external identity providers. Google, a widely used identity provider, allows users to authenticate and access applications effortlessly. In this blog post, we will delve into the process of integrating Azure AD B2C with Google accounts, empowering you to enhance identity management and elevate user authentication to the next level.
Google as an Identity Provider
Google serves as an Identity Provider (IdP) by allowing users to authenticate and access various applications and services using their Google accounts. As one of the most widely used identity providers, Google offers a convenient and familiar authentication experience for users.
The benefits of integrating with Google accounts,
Wide User Adoption:
Google has billions of active users, making it likely that many individuals already have Google accounts. By integrating with Google as an IdP, businesses can leverage this widespread adoption, allowing users to authenticate and access their applications easily using their existing Google accounts.
Streamlined User Experience:
Many people are familiar with using Google accounts to sign in to various websites and services. By integrating with Google accounts, businesses provide a seamless and familiar authentication experience. Users can skip the hassle of creating new accounts or remembering additional login credentials.
Robust Security:
Google places a strong emphasis on user account and data security. By integrating with Google as an IdP, businesses benefit from Google's advanced security infrastructure, including features like multi-factor authentication (MFA) and continuous monitoring. This ensures a high level of protection for user identities.
Single Sign-On (SSO) Capabilities:
Google as an IdP supports Single Sign-On, allowing users to authenticate once with their Google credentials and access multiple applications without repeatedly entering their login information. This enhances user convenience, reduces friction, and boosts productivity.
Trusted and Reliable Service:
Google is a reputable and trusted technology provider. Integrating with Google accounts as an IdP instills confidence in users, as they are familiar with Google's stringent security practices and reliable services. This trust in the authentication process contributes to a positive user experience.
Simplified Identity Management:
By integrating with Google as an IdP, businesses can offload the complexities of managing user identities and credentials to Google. This simplifies tasks such as password resets and account recovery, as users can rely on Google's robust infrastructure and self-service options.
Social and Personalization Opportunities:
Integrating with Google accounts provides access to user profile information, such as name, email, and profile picture. This data can be utilized to personalize the user experience, tailor content, and offer social features like sharing or social login.
Configuring Azure AD B2C for Google Integration
Step-1
Login into azure account and navigate to your Azure AD B2C tenant.
Step-2
Now select the "Identity providers" option from left menu.
Step-3
Within the "Identity providers" section, choose "Google."
Step-4
Now you will have below screen in front of you. Please enter
name, and previously selected
client Id and client Secret of the google application that we have created in
Part-4.
And we are done we have successfully configured the google account with AzureAdB2c tenant.
To test the integration click on "User Flows" option from left menu.
Now select "SignUpSignIn" userflow from the list.
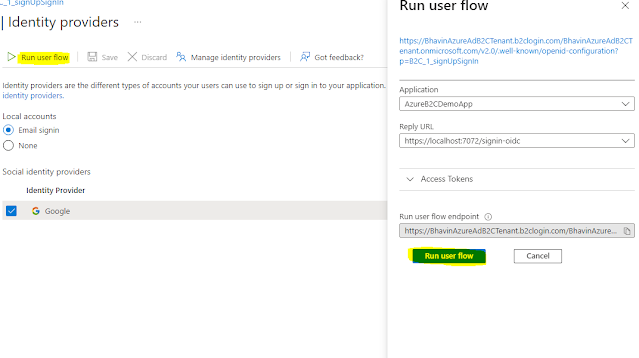
Now select "Identity Providers" from left menu and select "Google".
Now click on "Run User Flow" button from top. It will open new form on right side as below image.
Select "Application" and "Reply Url" from dropdown and click on "Run user flow" button.
It will open azure "Sign In" form.

So we have now google as a identity provider in the login form. Login into google account using your google credentials. It will redirect to the url that we have configured. So, in this way we can integrate google account in the azure ad b2c userflow.
Frequently Asked Question
Q: Why are user flows important in Azure AD B2C?
User flows are crucial in Azure AD B2C as they define the end-to-end user experience during authentication and registration. They enable businesses to customize and control the user journey, including the screens, options, claims, and validation steps, aligning it with their specific requirements and branding.
Q: What types of user flows are supported in Azure AD B2C?
Azure AD B2C supports various types of user flows, including:
Sign-up or sign-in: Allows users to create new accounts or sign in with existing accounts.
Profile editing: Enables users to edit and manage their profile information.
Password reset: Guides users through the process of resetting their passwords.
Email verification: Verifies the user's email address during registration or account recovery.
Multi-factor authentication: Adds an additional layer of security by requiring users to provide multiple authentication factors.
Q: How can user flows be customized in Azure AD B2C?
User flows in Azure AD B2C can be customized in several ways:
Customizing the UI:
You can modify the look and feel of the user interface, including branding, layout, and styling.
Adding or removing screens: You can add or remove screens to tailor the user flow according to your specific needs.
Collecting custom attributes:
You can collect additional user attributes beyond the default set provided by Azure AD B2C.
Defining validation and verification steps:
You can configure validation and verification steps, such as email verification or multi-factor authentication, to enhance security and user experience.
Q: How can user flows be implemented in Azure AD B2C?
User flows can be implemented in Azure AD B2C by defining and configuring them in the Azure AD B2C portal. This involves creating a user flow, selecting the desired flow type, customizing the settings and screens, and associating the user flow with the relevant applications or services.
Q: Can user flows be integrated with external identity providers?
Yes, Azure AD B2C allows integration with external identity providers, such as Google, Facebook, or Microsoft Accounts, within user flows. This enables users to sign in or sign up using their accounts from these providers, extending the authentication options available in the user flows.
Q: Are there any limitations or considerations when working with user flows in Azure AD B2C?
Yes, some considerations include:
- Carefully plan the user experience and flow to align with your application's requirements.
- Understand the specific requirements and guidelines of the identity providers you intend to integrate within your user flows.
- Regularly review and update your user flows to align with any changes or updates in Azure AD B2C.
- Please note that the above information is a general overview, and the specific steps and configurations may vary based on the current offerings and documentation from Microsoft. It's always recommended to refer to the official documentation and guidelines provided by Microsoft for the most accurate and up-to-date information.
Hope this will be informative blog. In next blog we will understand what is user flow in details.
Please, provide your valuable feedback if you find this blog useful or need anything to be changed.
See you in next blog 😀.







Comments
Post a Comment